Data Protection Impact Assessments (DPIA)
Readiness and Data Protection Impact Assessments
- GDPR Article 25: Data protection by design and by default
- GDPR Article 35: Data Protection Impact Assessment
The rules surrounding Data Protection Impact Assessments are sometimes the most confusing of the numerous new procedures introduced by the General Data Protection Regulation (GDPR). Many businesses do not understand what the paperwork is for or when necessary.
GDPR requires that data privacy be considered before implementing a project or a process. If the project or process is deemed to be high-risk, GDPR requires conducting a Data Protection Impact Assessment (DPIA) to meet compliance.
What is Data Protection Impact Assessment
When your organization gathers, maintains, or utilizes personal data, the people whose information you are processing are put at risk. These dangers vary from personal data being stolen or mistakenly leaked and used by criminals, impersonating the individual or individuals becoming concerned that their data will be used for unknown reasons by your organization.
A Data Protection Impact Assessment (DPIA) is a procedure that identifies and mitigates risks associated with the processing of personal data as early as feasible. DPIAs are critical tools for Data Protection Officers (DPOs) to reduce data breaches cybersecurity risks and show GDPR compliance.
A DPIA will raise awareness in your organization about the data security risks connected with a project. This will assist you in improving the design of your project, your GDPR readiness, and communication with essential stakeholders regarding large-scale data privacy threats.
GDPR Article 25: Data Protection by Design and by Default
The European Union GDPR compels you to consider data protection and all aspects of your data processing activity. This method is known as ‘data protection by design and default.’
It is an essential component of the GDPR’s risk-based strategy and emphasis on responsibility, i.e., your capacity to demonstrate how you are complying with its rules to prevent privacy risks.
In reality, this involves including or “baking in” data protection into your processing operations and business processes from the design stage through its lifespan.
Data privacy by design entails thinking about data protection and privacy problems from the start in everything you do. It may assist you in ensuring compliance with the essential principles and obligations of the GDPR, and it is part of the focus on responsibility.
GDPR Article 35: Data Protection Impact Assessment
As stated in article 35 of the General Data Protection Regulation, “Where a type of processing, in particular, using new technologies, and taking into account the nature, scope, context, and purposes of the processing, is likely to result in a high risk to the rights and freedoms of natural persons, the controller shall, before the processing, carry out an assessment of the impact of the envisaged processing operations on the protection of personal data.”
This assessment is known as a Data Protection Impact Assessment, and before you undertake any form of processing that is “likely to result in a high risk,” you must conduct a DPIA. This implies that, even if you haven’t determined the precise amount of risk, you should look for indicators that hint at the possibility of a widespread or substantial impact on individuals.
The GDPR specifically states that you must conduct a DPIA if you intend to:
- Utilize comprehensive and systematic profiling with significant consequences;
- Analyze particular category or criminal offense data on a big scale; or
- monitor publicly accessible areas on a large scale.
How do you conduct a data protection impact assessment?
Article 35(7) of the GDPR, as well as recitals 84 and 90, specify the minimum characteristics of a DPIA:
- A description of the intended processing processes as well as the processing’s purposes
- A determination of the processing’s need and proportionality
- An assessment of the dangers to data subjects’ rights and freedoms
- Measures planned to:
- Address the dangers
- Prove that you comply with the Regulation.
The GDPR lays out a broad, generic framework for creating and implementing a DPIA. This provides scalability, allowing even the smallest data controllers to develop and implement a DPIA, as well as flexibility, allowing the data controller to define the DPIA’s exact structure and form, allowing it to fit into existing working habits.
Beyond the essential features described above, the GDPR does not mandate the specific process for conducting a DPIA, allowing for scalability and flexibility in line with your organization’s needs. Although there is no one-size-fits-all strategy, the following steps can help you get started.
First, determining Whether Or Not A Dpia Is Required.
As described above, the GDPR states that your organization has to do DPIA when their profiling process is likely of “high risk,” specifically when it utilizes comprehensive and systematic profiling with significant consequences, analyze particular category or criminal offense data on a big scale, or monitor publicly accessible areas on a large scale.
Defining The Project’s Characteristics To Allow For A Risk Assessment To Take Place.
Early in the DPIA project, you should figure out how the project will acquire, store, use, and erase personal data. This exercise should also determine what information will be used in the project and who will access it.
This step aims to understand better how the information will be used as part of a project at each stage. This is necessary to recognize the data privacy risks caused by a project and determine what measures to mitigate those risks.
Identifying Data Security And The Threats That Come With It.
This stage entails reviewing the project design to determine what data protection issues the project raises, as well as any hazards it may expose individuals to, and any data protection-related threats the project may represent to your organization.
A new initiative has the potential to compromise or jeopardize an individual’s data privacy in a variety of ways. Risks range from the potential to cause distress, upset, or inconvenience to the possibility of financial loss or physical danger. In addition, there is a plethora of data privacy-related risks for businesses, ranging from compliance concerns to commercial considerations.
Identifying Data Security Solutions To Mitigate Or Remove Threats.
This stage builds on identifying data protection issues at stage 3 to reduce the project’s data privacy risk as much as possible.
Although it will virtually never be feasible to eliminate data protection risks, the goal of this stage is to balance such threats against the project’s goals, ensuring that any dangers accepted are proportionate to the project’s achievements.
If there are any significant residual risks under GDPR, you must communicate with the Data Protection Commissioner, as indicated below. Steps that can be taken to lessen the likelihood or severity of data privacy threats are known as data protection solutions.
During this stage, you should look for “data protection solutions” to lessen the project’s effect on data protection. This should be accomplished by examining each of the risks identified in the previous stage of the DPIA process and attempting to solve them individually or as part of a privacy solution that may address several concerns concurrently.
Signing Off On The DPIA’s Findings.
The fundamental goal of a DPIA is to identify and mitigate the data protection risks associated with a project. However, as stated throughout this guide, keeping a record of all activities done as part of the DPIA will ensure that the process is completed fully and reassure stakeholders that all data protection concerns have been considered.
This written record should also serve as the foundation for implementing the data protection solutions that have been selected, and it may be used to check off the implementation of each solution.
Data Security Solutions’ Integration.
Once approved, it is required to put the DPIA findings into action by incorporating any necessary adjustments into the project’s plans.
The earlier the DPIA can be completed, the easier it will be to put the data privacy solutions into action; however, because the DPIA is typically not finished until the project has already progressed somewhat in the planning stages, it will usually be necessary to adjust plans to put the data privacy solutions identified into action.
As part of the DPIA implementation, you should consider data privacy considerations. In addition, you should specifically evaluate if the data protection measures provided have the desired effect of minimizing data security threats.
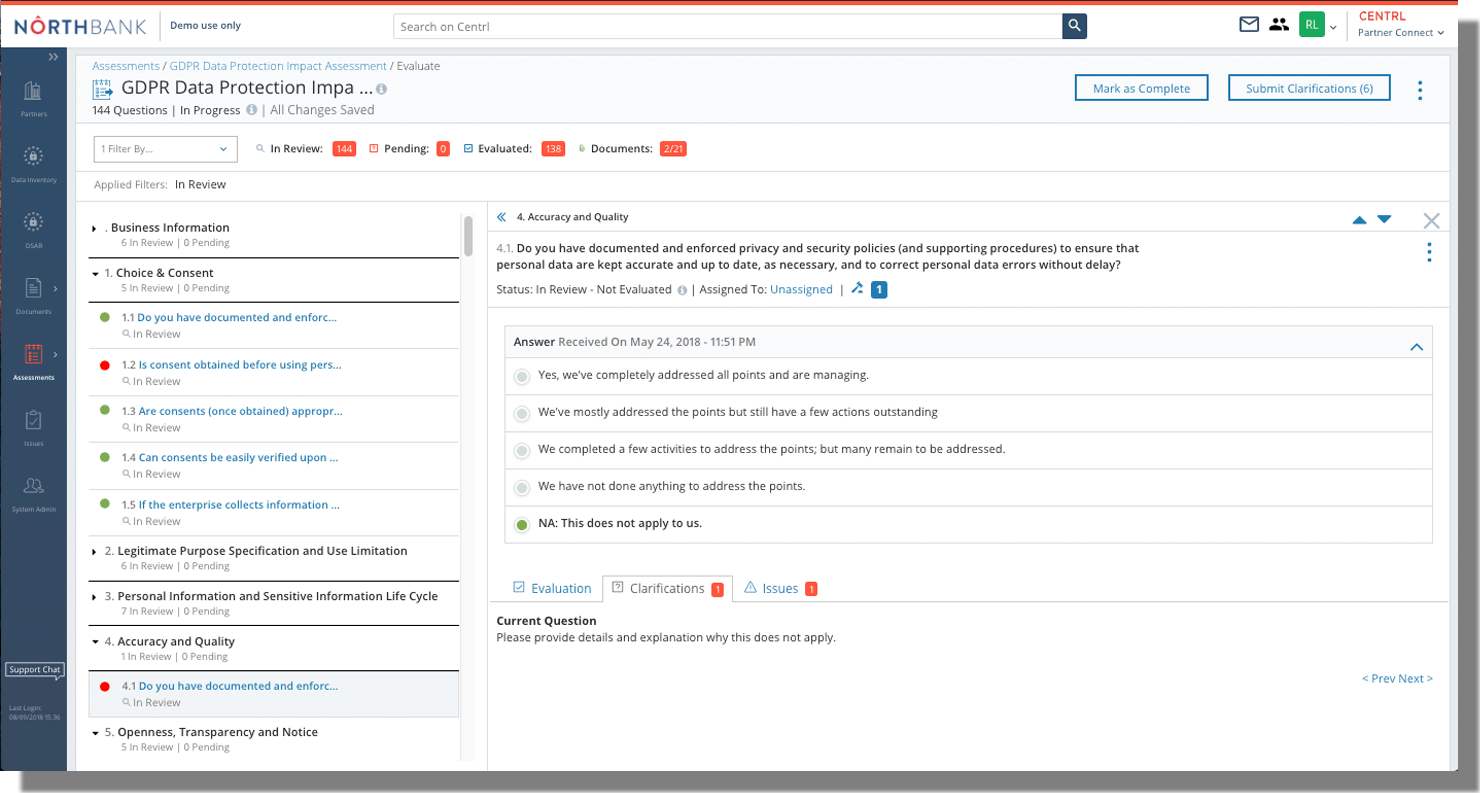
Benefits of CENTRL’s Privacy360
Single platform for automating all types of assessments
- Single platform for conducting readiness, impact, and third-party risk assessments.
- Integrated third-party assessments and audits that have access to data.
Assessment module full integrated with other privacy modules
- Assessment module integrated with Data Inventory, DSAR, and other modules.
- See 360 view of risk at the data subject, processing activity, and partner level.
Use standard assessment templates or upload proprietary ones
- Select from a library of industry-standard templates.
- Upload your templates and customize them with easy-to-use options.
Automate the whole assessment process
- Schedule assessments - including recurring - with automated publishing capability.
- Attach evidence requests by control or question.
- Automate grading with custom grading scales.
- Full assignment workflows.
- Manage clarifications in the application.
Track issues and manage the process to remediation
- Identify and segment issues and gaps linked to assessments.
- Document issue severity, status, and recommendations.
- Publish issues to third-party or internal departments.
- Manage the process to resolution.
Reporting and analytics
- Dashboards and reports to highlight risks and exceptions.
- Drill down to control risk level.
- Run comparison and detailed time-series analyses.
By using CENTRL’s Privacy360, your organization can easily manage a multitude of templates, checklists, and questionnaires while providing the control to monitor, evaluate and create audit reports allowing you to focus on the results instead of the process.
Read more about Privacy360, or contact sales about CENTRL’s privacy solutions.


